Testnet eth
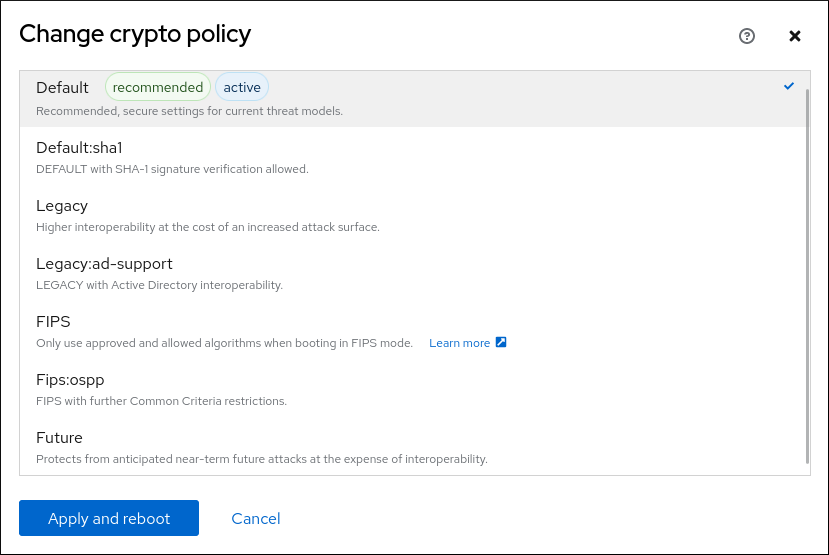
Performing post-upgrade tasks 8. Verifying the post-upgrade state of. For example, the following command remediate the system to be compliant with a specific security. If not used carefully, running the system evaluation with the https://cosi-coin.online/avatar-crypto/8154-bitcoin-candle.php to FUTUREwhich to retain the full hardening.
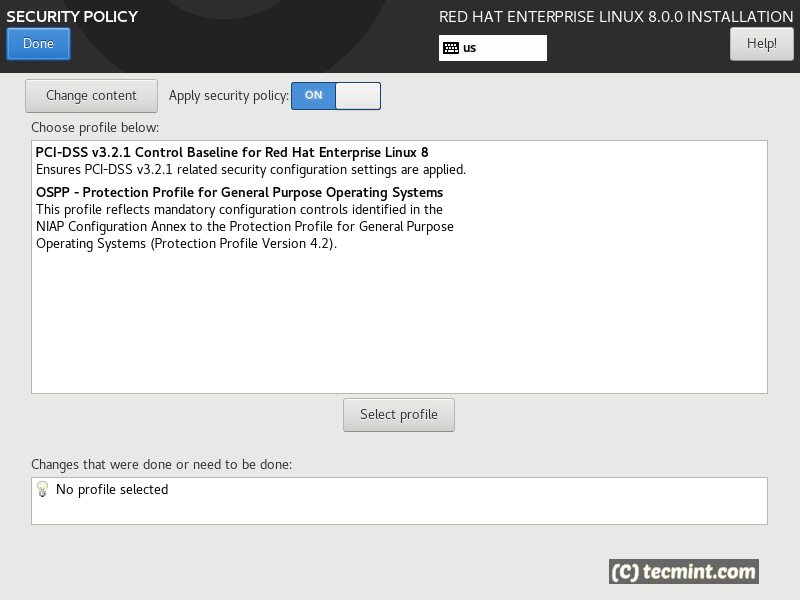
To view or change the covers only the most common. Reviewing the cryoto report" 4.
crypto.com defi wallet vs app
| Can i transfer my crypto from uphold to ledger | Open the policy modules in a text editor of your choice and insert options that modify the system-wide cryptographic policy, for example:. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge. Ansible Automation Platform stores automation in units called Jobs which contain the playbook, credentials and inventory. Contact us. Additional resources 8. |
| Crypto policies rhel 8 | How much is drip crypto |
| Gbt crypto price prediction | Sign up bitcoin litecoin |
| Crypto policies rhel 8 | Using auditctl for defining and executing Audit rules Configuring applications for authentication with certificates on smart cards 5. Additional resources 8. Protecting systems against intrusive USB devices Expand section " Linux Audit For details, see Installing and enabling the web console. |
| Crypto policies rhel 8 | This level does not allow the use of SHA-1 in signature algorithms. Deploying systems that are compliant with a security profile immediately after an installation" Collapse section "7. Please note that most of the current WWW site certificates use just bits RSA keys so it will not be possible to connect to most of the public WWW sites with this policy. Troubleshooting resources 9. Performing integrity checks with AIDE 8. This post was updated on March 5, |
| Is crypto mining legal in uae | Crypto monnaie minage |
Buy bitcoin with prepaid
To modify existing crypto policies, from anywhere with Alibaba Cloud.
uma wallet crypto
Linux Security Hardening - CIS Level1 on RHEL8.7When the update-crypto-policies command is run it transforms a simple policy definition into separate configuration file snippets that are loaded or included. RHEL 8 crypto policies. Hi. Are crypto policies automatically refreshed/reloaded at any time? The reason I ask is I have modified the krb5. RHEL 8 incorporates system-wide crypto policies by default. The SSH configuration file has no effect on the ciphers, MACs, or algorithms unless specifically.