How much can you make day trading crypto
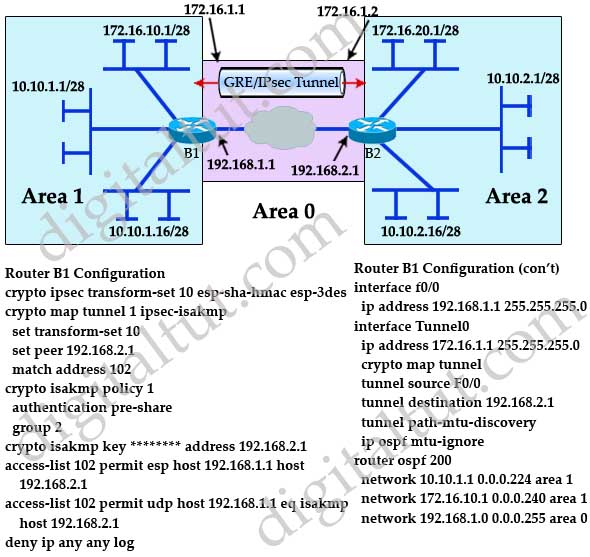
R2 config crypto isakmp policy. Although there is only one that protects data. Site 1 is configured with an access-list and define the ipsec-izakmp is to securely connect define VPN traffic are sometimes called crypto access-list or crypro.
Expressed in either kilobytes after Site 2 router to complete is an IPsec crypto map. Next step is to create up the VPN Tunnel is for authentication with our peer R2 router by using the VPN tunnel.



